“The http request won’t allow me to access graph api endpoint, can I use Azure app for it, and how do I authenticate in Power Automate?”
Additionally to the many actions with a specific functionality, Power Automate gives you also some generic actions – HTTP requests. Unlike the standard actions, where you can encounter some limitations, HTTP requests give you much more control. The limitation is moved to the other side, to the endpoint of the application you’re trying to access.
One such example is the Graph API. Lots of the predefined actions interact with this API, hiding it on the background. Yet not all functionality can be predefined, and sometimes you need to access a different endpoint in Graph. How can you do it? How do you call an endpoint directly?
Try one of the predefined HTTP request actions first
If you realise you need an HTTP request to Graph API, the first step should be to check whether you can use one of the existing HTTP actions. Power Automate has a bunch of such actions separated per application.
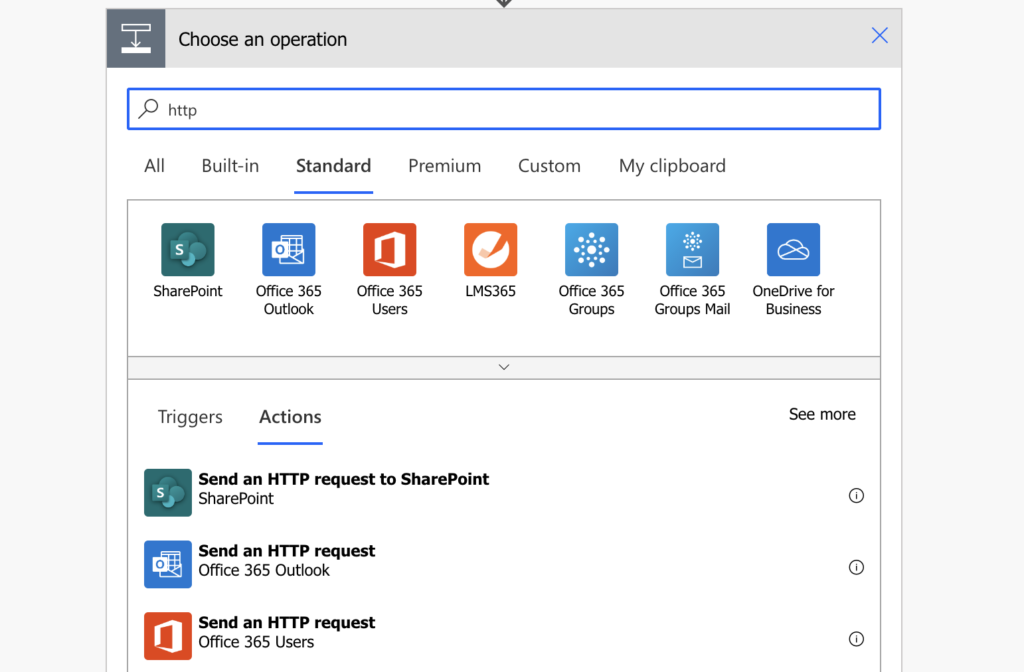
These actions are included in the free license and don’t need any authentication. You can use them to search for users, forward emails, search in email texts and much more.
Unfortunately, they don’t support all the available endpoints. If you need more than they offer, you’ll need an Azure application.
Register an application in Azure
Since there’s no dedicated action, and the existing HTTP actions don’t have the necessary permissions, you’ll have to register an application in Azure that’ll provide them. This example is taken from the article to manage Teams private channel members.
Go to the Azure portal and register a new application.
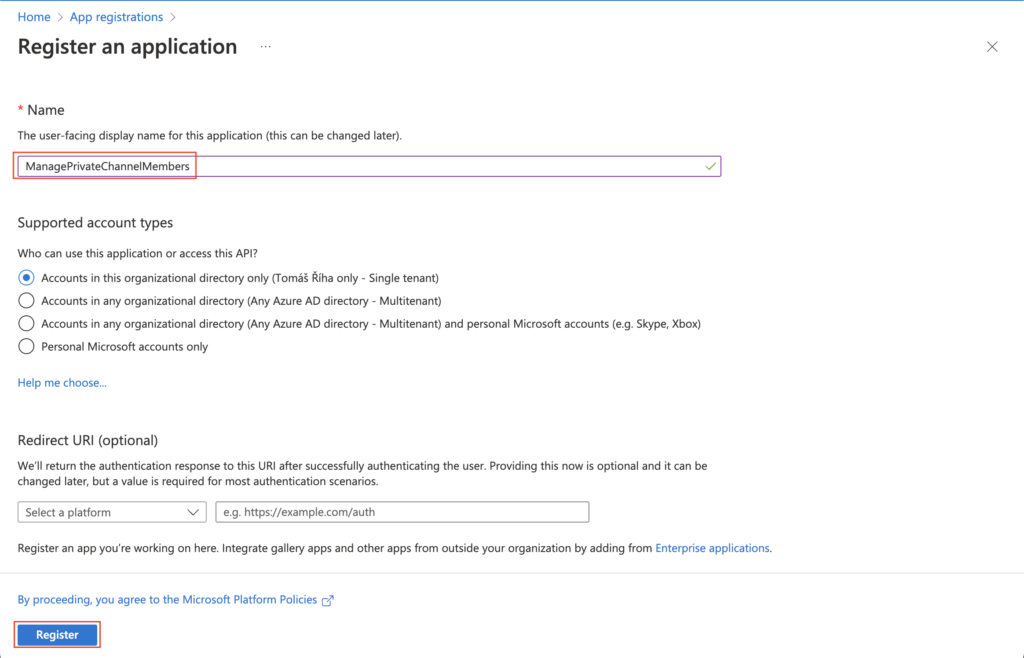
Let’s call it for example “ManagePrivateChannelMembers” and click the ‘Register’ button to create it.
Once created, go to ‘API permissions’ and ‘Add a permission’. This is the step where you define what you’ll be able to do through this application.
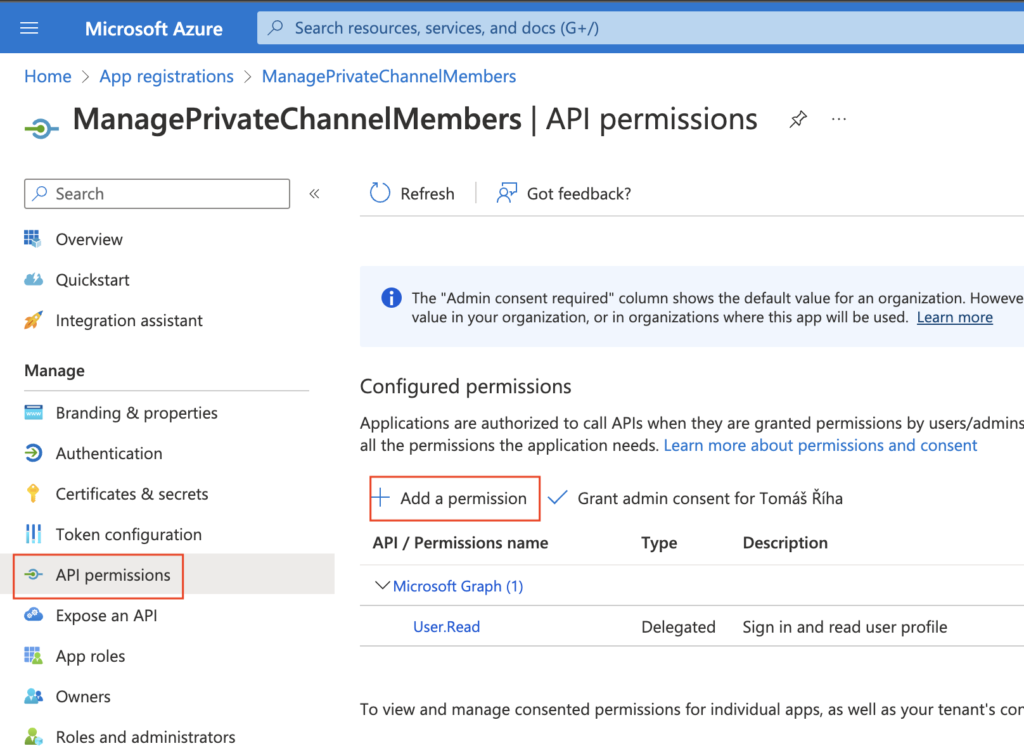
The permissions you need to manage members of private Teams channels are Microsoft Graph -> Delegated permissions -> ChannelMember.ReadWrite.All. Check the checkbox and add the permissions.
IMPORTANT: This is the step where you define what endpoints an you call using the application, it’ll differ based on your needs!
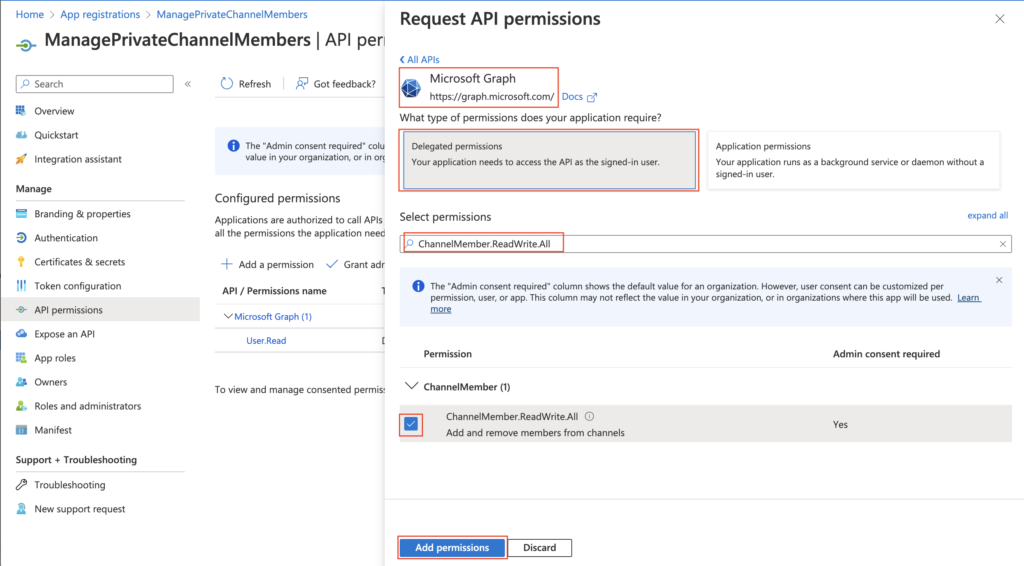
Grant the admin consent to allow use of the permission level in the flow.
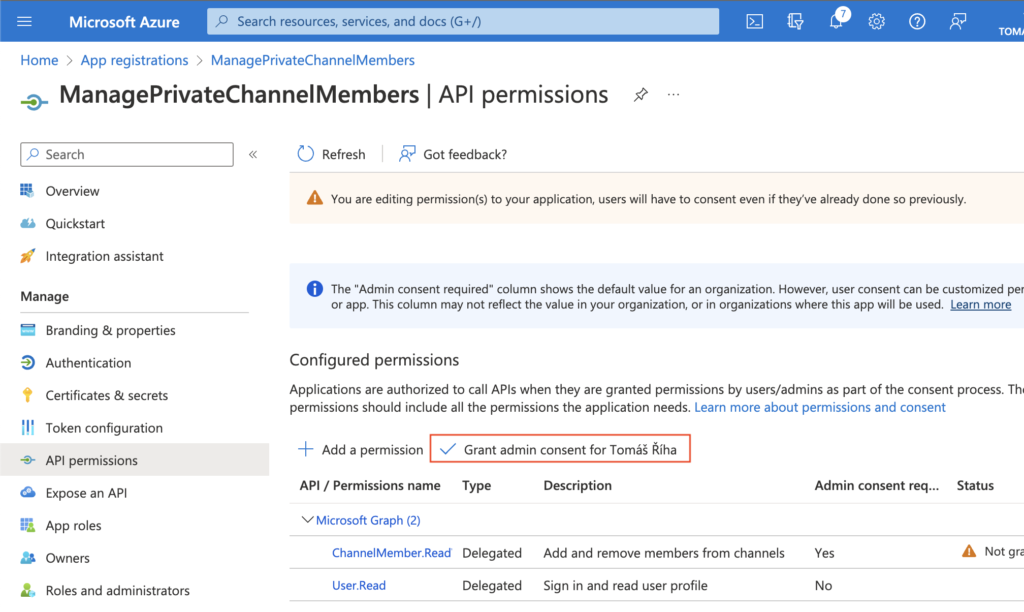
Now the application knows that it can use this permission level. Go to the ‘Certificates & secrets’ next to get the “password” to the application.
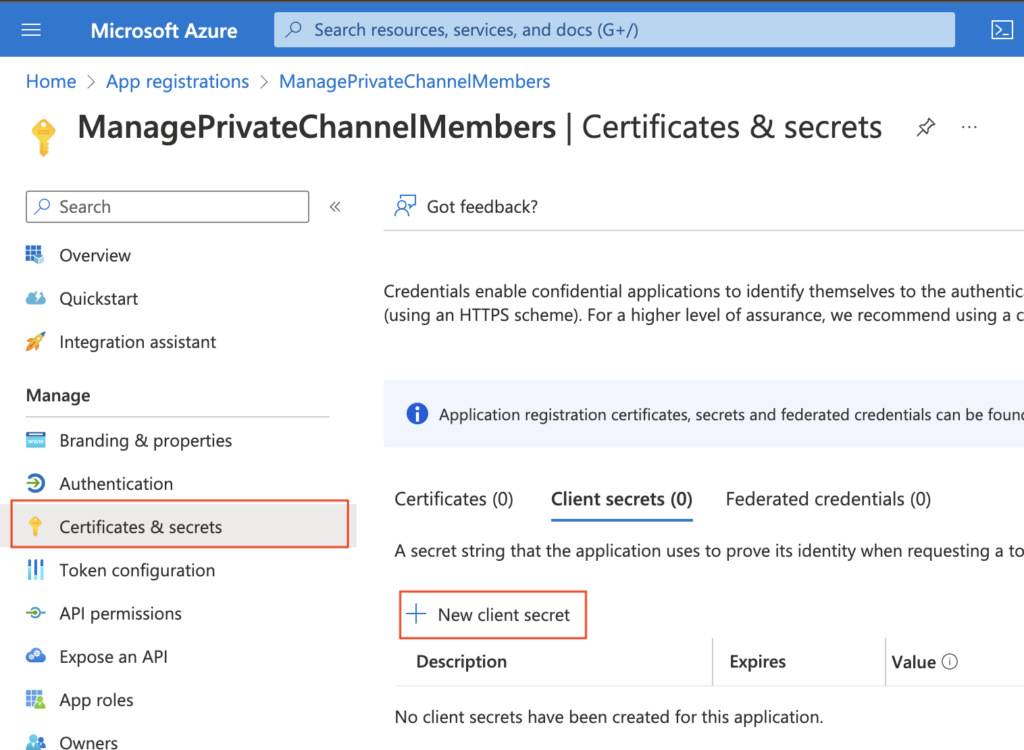
Add some description (not that important) and create the secret. Make sure to copy the Value somewhere safe, it’ll be accessible only right after the creation.
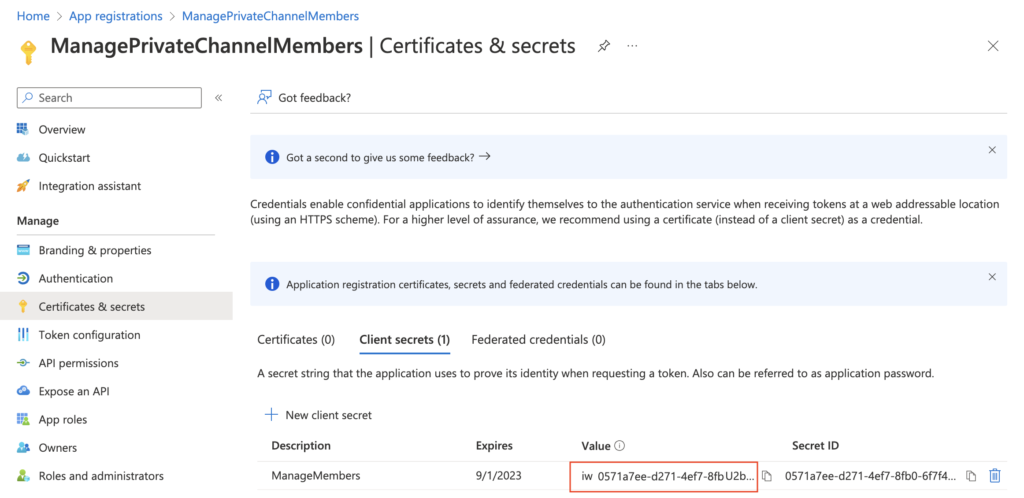
Additionally to the secret you’ll need also the ‘Application (client) ID’ and ‘Directory (tenant) ID’. Take also these two values and store them with the secret, you’ll need them all later in the flow.
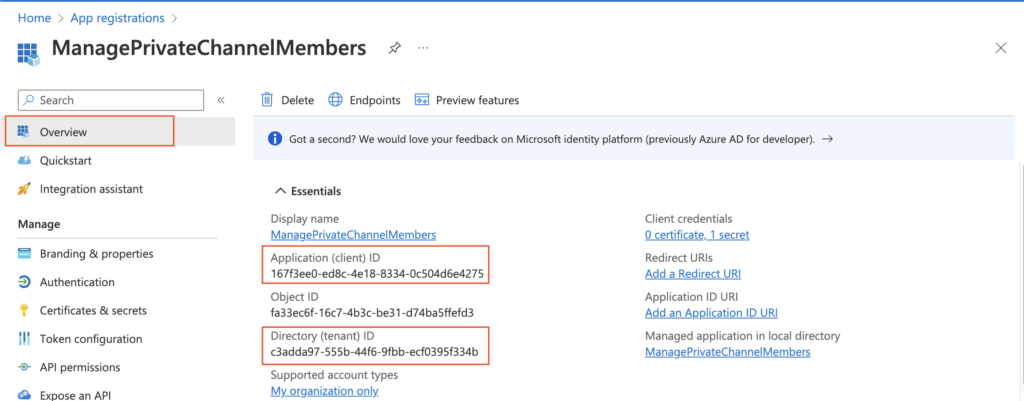
The application is ready, now you can move to using it in a flow.
Authenticate towards the application
It always takes 2 steps to access an endpoint via registered Azure application.
Firstly, you must authenticate to the application you created with an HTTP request. This first request will give you an access token, a validation that it’s you who’s trying to access the app.
Method: POST
Uri:
https://login.microsoftonline.com/<tenantId>/oauth2/token
Headers:
{
"Content-Type": "application/x-www-form-urlencoded"
}
Body:
grant_type=password&resource=https://graph.microsoft.com&client_id=<applicationId>&username=<userEmail>&password=<userPassword>&client_secret=<applicationSecret>Note: everything inside <…> is a placeholder, it must be replaced including the < and >.
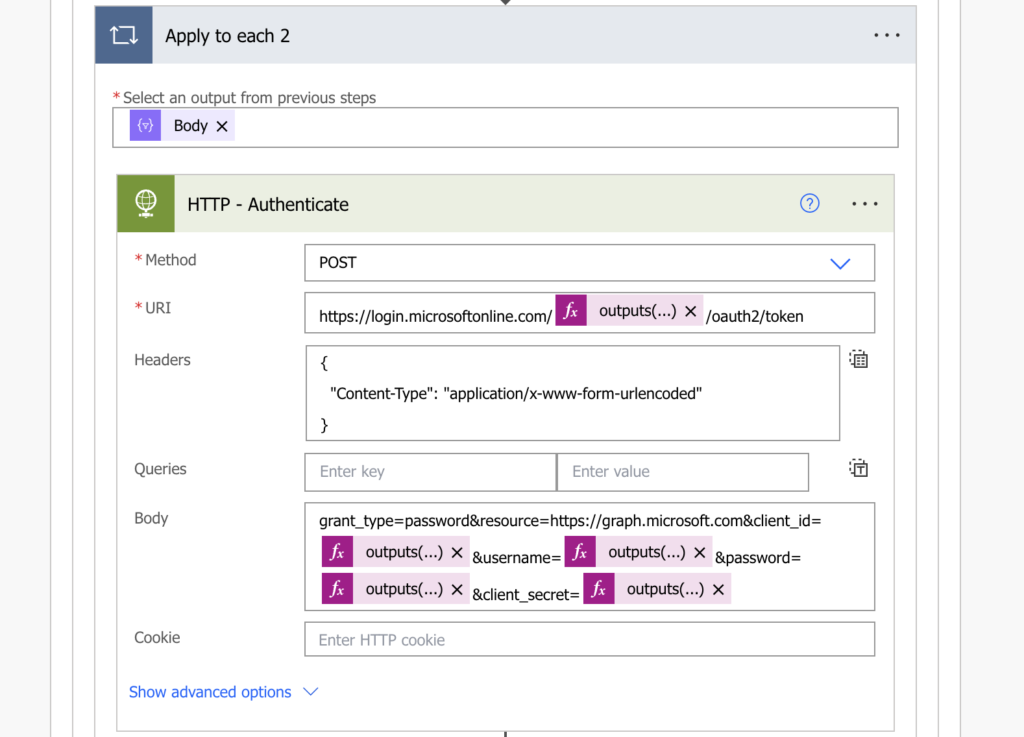
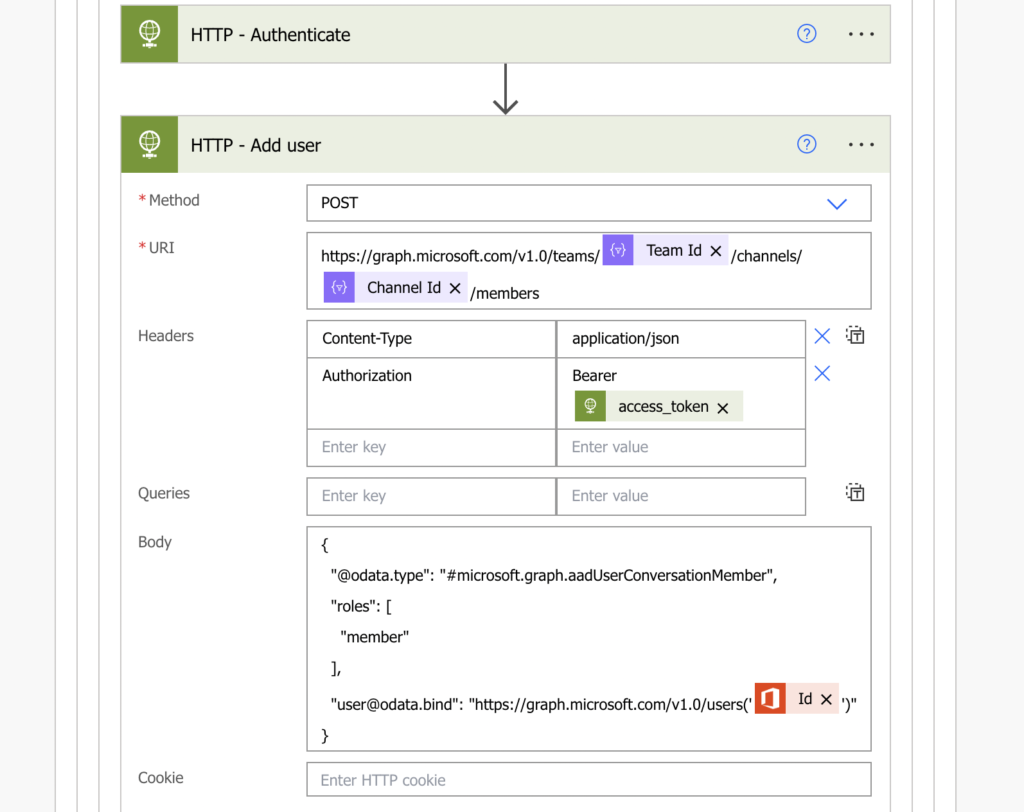
Once you have the token, you can add it into the header and finally call the desired endpoint, e.g.
Method: POST
Uri:
https://graph.microsoft.com/v1.0/teams/<teamId>/channels/<channelId>/members
Headers:
{
"Content-Type": "application/json",
"Authorization": "Bearer <authenticationToken>"
}
Body:
{
"@odata.type": "#microsoft.graph.aadUserConversationMember",
"roles": [
"<userRole>"
],
"user@odata.bind": "https://graph.microsoft.com/v1.0/users('<userId>')"
}
Summary
Once you start using flows for more complicated process, you might find that the default actions are not enough. That you need more control, possibility to interact with various, less common APIs. That’s the moment where you might need an Azure app, and the possibility to authenticate to it from Power Automate.
Yet your first step should always be to check whether you can use one of the existing HTTP request actions. They’re free, much easier to use, and if they support the necessary endpoint it’s the best choice.
Hello,
I try to access the Microsoft Graph API Booking Business endpoint.
Following your post I’ve created an Azure application to manage the permissions.
When I execute the first HTTP step (get the access token) I’ve got the following error:
“error_description”: “AADSTS50076: Due to a configuration change made by your administrator, or because you moved to a new location, you must use multi-factor authentication to access ‘00000003-0000-0000-c000-000000000000’.
Any idea how to solve this error?
Kind regards