“It was so easy to manage item permissions in SharePoint 2010 flow, but in Power Automate I’m confused from all the HTTP requests and REST API .”
While you could manage permissions easily in SharePoint 2010 flow, in Power Automate it’s a different situation. Now you’ve got two options how to handle the permissions. A simple one using dedicated Power Automate actions and a complex one with HTTP requests and REST API. This post will be about the dedicated Power Automate actions.
Stop sharing an item or a file
The ‘Stop sharing an item or a file’ action breaks permission inheritance and removes permissions from all users and groups, except the ones with Full Control. That means all the Admins / Owners / Users who had Full Control on the list / library before the action will keep it. All it needs is the ID of an item or a file.
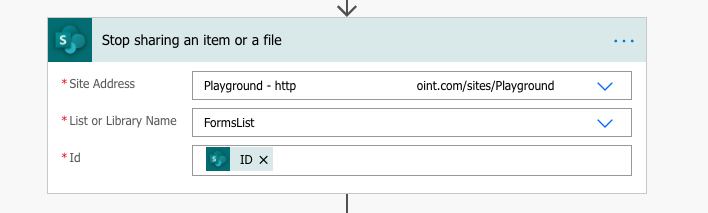
To achieve the same functionality via REST API you’d need at least 4 HTTP requests.
1. break permission inheritance
_api/web/lists/getByTitle('ListName')/items(ID)/breakroleinheritance(true)
2. get all current permissions
_api/web/lists/getByTitle('ListName')/items(ID)/roleassignments
3. remove all current permissions (with "X-HTTP-Method": "DELETE" header, in a loop)
_api/web/lists/getByTitle('ListName')/items(ID)/roleassignments(UserOrGroupID)
4. assign back Full Control to Owners / Admins / Users
_api/lists/getByTitle('ListName')/items(ID)/roleassignments/addroleassignment(PrincipalId=UserOrGroupID,roleDefId=FullControlRoleID)Limitation
I heard a complaint that the action keeps the Full Control permissions. That you don’t have control over it. That you can’t remove access for users with Full Control. But I don’t think it’s a valid complaint. If you need to remove users with Full Control, they probably shouldn’t even have Full Control in the first place.
Grant access to an item or a folder
‘Grant access to an item or a folder’ action is the next step after the ‘Stop sharing an item or a file’ action. You removed all permissions from the item or file, but now you need to give some of them back. This action needs a bit more than just an item ID. You have to enter also recipients (users) and Roles to assign. By default it offers only 2 roles in a dropdown: Can edit (Edit permission level) and Can view (View permission level).
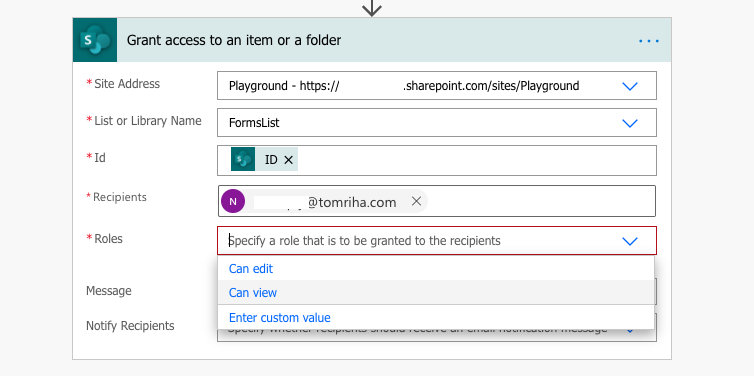
Luckily, you can define also your own ‘Roles’ value for the other permission levels, including your custom ones. For example, to assign Read permission level.
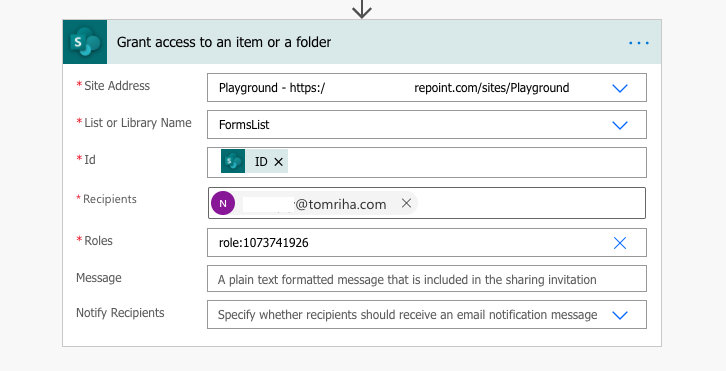
This action doesn’t replace as many REST API HTTP request as the one before, but it’s still a few.
1. get user ID
_api/web/siteusers/getbyemail('userEmail')
2. assign permissions to user
_api/lists/getByTitle('ListName')/items(ID)/roleassignments/addroleassignment(PrincipalId=UserID,roleDefId=RoleID)Permission level IDs
As already mentioned, you don’t have to stay with Edit and View permissions, but you can use all the permission levels available on your SharePoint site. Below you can see a table with the default RoleIDs.
| Default permission level IDs | |
| Full Control | 1073741829 |
| Design | 1073741828 |
| Edit | 1073741830 |
| Contribute | 1073741827 |
| Read | 1073741826 |
| Approve | 1073741927 |
| View | 1073741832 |
You can also find all of the permission level IDs, including your custom levels, using browser, REST API (_api/web/roledefinitions), and search (<d:name>).
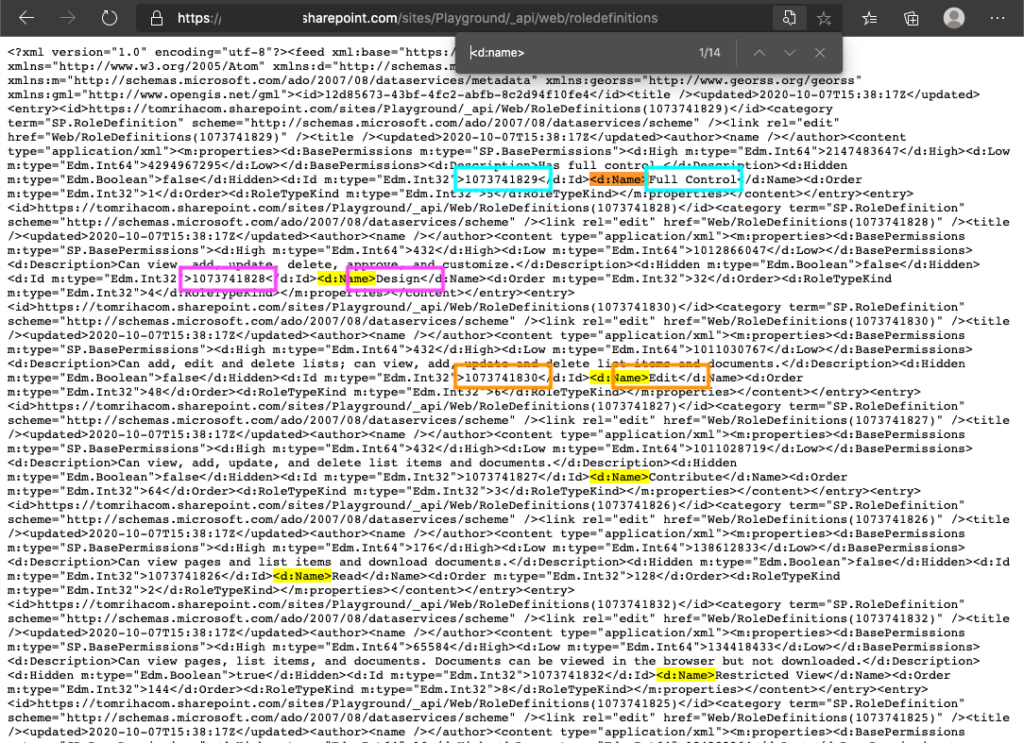
Limitation
As already mentioned, you can assign permissions only to users (with email address). That means users and Microsoft 365 group. You can’t assign permission to SharePoint group using this action, that’ll always need an HTTP request.
Summary
In my opinion the ‘Stop sharing an item or a file’ action is a good starting point for all permissions setting flows. It saves a lot of HTTP requests and the other related actions.
Not so is the second dedicated action ‘Grant access to an item or a folder’. It’s not a full replacement for the HTTP requests to assign permissions, you’ll still need those for SP groups. But if you use it, it’ll still do some of the work, just don’t expect miracles.
Hello,
Thanks for sharing this useful article.
I tried provided steps. I am getting 404 – File or directory not found. error at the step to assignment of permission.
Hello Ali,
I’d check if the item with the ID exists in the list/library, if you have the action configured correctly.
Hi Tom,
This is great article, exactly what I looking for!!!
This work great since we would like to restrict the access to limited users. Just one question, when there is new person joining the SharePoint site/ lists, he/ she would be able to see all items created in the past correct? Is there a solution on this?
Thanks in advance for your support!
Hello Soon Keang,
it depends whom you assign the permissions:
– If you assign the permissions directly to users, only the selected users will have access.
– If you assign the permissions to a Microsoft 365 or Mail-enabled security group then every new member of that group will have access (and this is a preferred solution).
Hi Tom,
thanks for your article!
However I have a question: We are using document sets and the “stop sharing an item or file” action results in a JSON error. Therefore I’d like to use the REST API to remove all permissions on a document set.
Can you do it without using IDs? I just want to remove every single R + R+W permission on the document set and set the permissions later on in the flow with the “Grant access” action.
You describe it in your article with “(with “X-HTTP-Method”: “DELETE” header, in a loop)” – can you help me how to build this in Power Automate?
Your help would be greatly appreciated, thank you! 🙂
Hello Nico,
did you check the other post on managing permissions on folders (as document set is basically a folder): https://tomriha.com/how-to-remove-permissions-from-a-sharepoint-folder-with-power-automate/? The ‘Stop sharing…’ actions don’t work on folders so I guess it’s expected that it won’t work on document sets either. But the http requests should work on both.
Hello Tom.
sorry for the late reply, been busy weeks.
Just wanted to let you know that this worked perfectly fine. I didn’t see the other post, my bad.
Thank you so much!
I hope you have great week! 🙂
Dear Tom,
If it is not too much bother, I would like to share with you a strange experience I am having with the “Recipients” field of the “Grant access to an item or a folder”. I have an automated Flow that, among other things, grants access to items in a SharePoint XML forms library hosted on SharePoint Online. The library uses an InfoPath form (which is not going away anytime soon), and contains a list of Approvers created using a People Picker in a repeating section. However, as an InfoPath promoted property, only the user name of each approver (no e-mail address) is saved in the form and, thus available to the Flow.
My Flow uses “Search for users (V2)” (Office 365 Users) to locate the current Approver’s e-mail, which I extract into a variable and then use that variable in the “Recipients” field for granting access. This works nearly all of the time, but the Flow crashed on the “Grant access etc.” step with the error “Couldn’t resolve user George.Washington@MyOrg.com“. When I looked at the JSON returned from “Search for users (V2), I see that there are actually two properties that contain e-mail addresses for a User:
“Mail” and “UserPrincipalName”. Moreover, the e-mail addresses of this user, though similar, are different. The “Mail” property holds an address in the format “FirstName.LastName@MyOrg.com”; the UserPrincipalName property holds an e-mail address in the form FirstInitial and LastName (e.g.: GWashington@MyOrg.com“).
I am not certain whether the e-mail address in the UserPrincipalName will work either, but it must, since the Current Approver was initially selected using a People Picker which uses the same address list as Outlook.
Any thoughts on how to resolve this? Somehow trapping the error of the “Grant access etc.” when it fails on “Mail” and re-trying it with “UserPrincipalName”, perhaps?
I appreciate any insights you can offer.
Sincerely,
Joseph Davoli
Hello Joseph,
unless your Active Directory is a mess, it should be always the same user property – either the Mail or the UserPrincipalName property for all the users. But if you’d like to try both of the values, you can do it as you described. Try one of the properties first, and if it fails, try the other one.
Each Power Automate action allows a run after configuration (shown e.g. here: https://tomriha.com/3-ways-to-disable-an-action-or-a-section-of-a-flow-in-power-automate/). You can:
Dear Ton,
First I would like to thank and congratulate you for the content made available here, it is of great help.
I have a question about collecting all objects from a parameter, as in the example below:
I would like to return all blocks that contain “GroupId” = “00G5f000000PMOOEA4”.
[
{
“@odata.etag”: “”,
“ItemInternalId”: “04bee7bb-3350-456e-a5c8-9e24b”,
“GroupId”: “00G5f000000PMOLEA4”,
“Id”: “0115f0000000yolAAA”,
“SystemModstamp”: “2022-01-10T03:39:18Z”,
“UserOrGroupId”: “0055f000007Vz7sAAC”
},
{
“@odata.etag”: “”,
“ItemInternalId”: “4279baa9-5ea5-4002-96b0-30a1e8”,
“GroupId”: “00G5f000000PMOQEA4”,
“Id”: “0115f0000000yp6AAA”,
“SystemModstamp”: “2022-01-10T03:50:50Z”,
“UserOrGroupId”: “0055f000007Vz7iAAC”
},
{
“@odata.etag”: “”,
“ItemInternalId”: “1fc4afd9-9969-4eac-a168-7ed381”,
“GroupId”: “00G5f000000PMOKEA4”,
“Id”: “0115f0000000yxOAAQ”,
“SystemModstamp”: “2022-01-10T12:44:38Z”,
“UserOrGroupId”: “0055f000007W2JfAAK”
},
{
“@odata.etag”: “”,
“ItemInternalId”: “0389fe40-908c-4261-9ce5-778eef”,
“GroupId”: “00G5f000000PMOOEA4”,
“Id”: “0115f0000000yxnAAA”,
“SystemModstamp”: “2022-01-10T12:46:00Z”,
“UserOrGroupId”: “0055f000007W2JeAAK”
},
{
“@odata.etag”: “”,
“ItemInternalId”: “205dc347-a75d-4d83-86e5-77bcdc,
“GroupId”: “00G5f000000PMOMEA4”,
“Id”: “0115f0000000yygAAA”,
“SystemModstamp”: “2022-01-10T12:57:01Z”,
“UserOrGroupId”: “0055f000007Vz7jAAC”
},
{
“@odata.etag”: “”,
“ItemInternalId”: “41439b91-955d-4015-acee-ed177”,
“GroupId”: “00G5f000000PNmqEAG”,
“Id”: “0115f0000000z0NAAQ”,
“SystemModstamp”: “2022-01-10T14:18:39Z”,
“UserOrGroupId”: “0055f000007Vz7gAAC”
]
The goal is to collect all “UserOrGroupId” that are in a given “GroupId”.
Thanks.
I ended up using the wrong topic to ask this question, I apologize.
Hello Caliel, 00G5f000000PMOOEA4.
use the ‘Filter array’ action to do that. Add the array of objects as the input, and filter only the items where GroupId
Once you have the items filtered, you can use ‘Select’ to extract only the UserOrGroupId from the remaining objects.
Hi thanks for the Approach..
can you tell me what if i want to add both email and sharepoint group for the item level permissions using people picker multi select option..
it has go on loop ..do you have any approach to get this
Hello Amar,
you can use this solution for individual users, but it won’t work with SharePoint groups – for those you’ll need HTTP requests: https://tomriha.com/how-to-add-permissions-to-sharepoint-group-with-power-automate/
But you’re right, you’ll need a loop to assign the permissions one by one.
Hi Tom
Great article, just wondering, I see that you have “_api/web/lists/getByTitle(‘ListName’)/items(ID)/roleassignments” listed, is there something that I can use where I can feed an email address and it would tell me what the highest access that person has?
My use case is that in power apps I want to show an edit button only when someone has permission to edit that item.
Cheers
Hello Daniel,
I don’t think you can do that, you can list all users/groups with access on the resource with an http request (_api/web/lists/getByTitle(‘PlaygroundList’)/items(9)?$expand=RoleAssignments/Member/Users&filter=Email) but I don’t know how you’d recognise which permission level is the highest one.
I thought “Grant access to an item or a folder” was going to solve my issue and it does work as described, but unlike “Create sharing link for a file or folder” it doesn’t provide an outputs you can grab.
I need to create a sharing link that I can parse down to an Excel file for a mailmerge. I can do this with “Create sharing link for a file or folder” but it doesn’t give the option of email restricted links.
So I’m falling between two stools here. Is there an alternative Action that will get me there?
Hello Simon,
if the actions don’t work I’d look for some http request, maybe it’s doable that way.